Cyber Awareness Survey – answers
1. William from IT telephones you advising that he is updating your user account – he needs your existing password to complete the update. What would you do?
· Tell William your password
· Ask William for a contact number and call him before disclosing your password
· Call the ICT Service Desk and ask for William before disclosing your password
· Refuse to disclose your password and call ICT Service Desk to report an incident
· Contact the ICT Service Desk for advice
· Contact the Information Governance Lead for advice
The correct answer is to refuse to disclose your password – you should never give out your password (or PIN or any other personal details) particularly if someone calls you out of the blue. It is also appropriate to notify the Service Desk and/ or the IG Lead so that they are aware of ‘phishing attempts’ that are taking place against you and your colleagues.
Asking for a contact number doesn’t protect you – a hacker may be quite happy to give you a mobile number which they will happily throw away once they have tricked you into disclosing your password.
2. Which of these do you think would make your best password?
· jobloggs
· x9$5Aa67@Ez%19
· BlueW1nter$ea
· Lincoln23
The strongest password is almost certainly x9$5Aa67@Ez%19 – but it is so complex you couldn’t expect to remember it, so you would have to write it down. The best password here is BlueW1nter$ea. It uses three random words so is easier to remember, but because you avoid a common phrase it is unlikely to be ‘cracked’. If you routinely swap certain letters for characters (change i to !, s to $ etc) you can create a really safe password that you will remember quite easily. You should avoid names and simply adding numbers to a password is not recommended as good practice.
3. You receive an unwanted spam email at work; on the bottom of the email it says that to unsubscribe, simply reply with ‘unsubscribe’ in the subject line. What would you do:
· Forward it to the ICT Service Desk
· Forward it to the IG Lead
· Ignore the email and delete it
· Reply to prevent future spam
The best response is to ignore it and delete it. If in doubt, forward it to the ICT Service Desk – they may be able to tinker with the anti-spam filters to stop similar emails getting through to you and your colleagues.
You should not reply to prevent spam – many spam emails are sent to randomly generated recipients. The sender doesn’t know that your email really exists, but as soon as you respond they know your email address exists, which is likely to result in you receiving more spam in the future.
4. You need to do some online banking with your bank,LoadsamoneyLtd. Which one of these
addresses would you use:
· www.loadsamoney.co.uk
· https://www.loadsamoney.co.uk
· http://www.loadsamoney.co.uk
· any of the above – they are all the same
The key point here is to look for a web address that includes https. This means that the site is secure – depending on your browser you may also see a padlock icon. This means that all information you type is scrambled before being sent and then unscrambled at the other end of the connection – anyone snooping on your website will only see gibberish. Lots of websites don’t need to be secure if they are just displaying non-confidential information, so don’t worry if you visit a site that just shows http… But never enter any sensitive, confidential or personal information unless you see the padlock or https – everything you type is being sent in plain text and could be seen by a hacker ‘sniffing website traffic’.
If in doubt, don’t follow links in emails – use a reputable search engine to look for the site you are interested in and follow the link from the search engine.
5. You need to complete some urgent work outside of work hours but don’t have a Trust laptop. What do you think you should do:
· Password protect the documents and email them to your home computer
· Use a file-sharing service such as Dropbox or OneDrive
· Request a laptop via your manager
· Request secure remote access, so you can access your files securely on any computer
· Transfer the documents to an encrypted memory stick
· Speak to the Information Governance Lead for advice
· I would not undertake Trust work outside work hours
The best option is to request a laptop via your manager or to request secure access so that you are working in a safe environment supported by the Trust. If in doubt speak to the Service Desk for advice.
There are risks with all of the other options – if you password protect a document or use an encrypted memory stick, this provides some protection against unauthorised access to information (for example if the memory stick is lost or stolen). But there is a risk that your document or memory stick is infected by a virus which is then transferred back to the Trust. The Trust is able to maintain a safe environment for you to work in, provided you use equipment and networks that are maintained or approved by the Trust. If you start to work outside these safe areas, the Trust cannot protect you, and you could potentially cause an infection or data breach for the Trust.
6. To help us understand if you have ever had to work-around the rules to get your work completed, have you ever done the following? Please tick any that apply – and please be honest. If you are having to find workarounds to get the job done, it is important that the Trust is aware of this – remember this survey is anonymous.
· I have password protected documents and emailed them to my home computer
· I have emailed documents to personal addresses without password protecting them
· I have used file-sharing services such as Dropbox or OneDrive, so that I can access work
documents on other computers
· I have copied documents to unencrypted memory sticks
· I have copied documents to an encrypted memory stick, but used them on personal devices
· Anything else that you felt was necessary to enable you to work effectively, but which you
suspect isn’t entirely legitimate
This question is designed to identify where staff feel that they have no option but to circumvent the rules. It is recognised that staff will focus on doing what they need to do to get the job done – and if there are barriers in their way (including lack of equipment or unwieldy systems and processes) it is human nature to look for workarounds. We are grateful to all staff that completed this question honestly.
7. You receive an email asking you to click the link shown (in the survey) – is it safe to click this link?
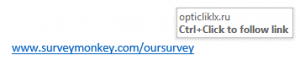
· Yes
· No
· Don’t know
This link is not safe – when you click over a link most browsers will display the destination that you will be taken to when you click your mouse. In this case the innocent looking surveymonkey link is going to take you to a suspicious looking Russian website.
You may also receive email addresses where the true identity of the sender is hidden – for example, if you bank with Barclays, you may receive an email that looks like it is from Barclays, but the full email address is help@barclaysbank.nastyscammers.com. Read the link from right to left – the true sender in this example is nastyscammers.com, not Barclays Bank.
Be careful to read the full link or email address and if you are ever in doubt regarding a link, don’t click it.
8. You are catching up on some emails in a coffee shop – which of these should you consider:
· Should I use the free wifi or my mobile connection?
· Should I have another muffin?
· Do I take the comfy chair by the window or the tall chair that is better for my posture?
If you are connecting to free wifi you need to be aware that it may not be secure. It may be cheaper to use someone else’s wifi rather than a mobile connection, but the mobile connection is private and secure. If you have a work laptop with a VPN available (virtual private network) this allows you to create a secure connection even over a public wifi. If in doubt, be very cautious and don’t send any personal, sensitive or confidential information over a public wifi.
The question about another muffin was a bit of a red herring – but of course you should remember to lock your laptop screen and never leave it unattended if you do succumb to the temptation of another tasty treat.
Think about where you are sitting and who can see your screen – the Trust has invested lots of money on clever technology to keep your equipment and your data secure – all of this is useless if you have confidential information displayed on your screen that anyone can read over your shoulder.
Important information: What to do if you think that a cyber-attack or security breach may be underway or the organisation may be at immediate risk of an attack:
During standard office hours – 8AM – 5PM (Monday to Friday)
· Contact the ICT Service Desk on 445800 or 01205 445800
Outside of these hours including weekends and bank holidays
· Contact the Site Duty Manager and advise them of the concern – this will then be escalated to the ICT Out of Hours Service
General enquiries or non-urgent concerns can also be sent to cybersecurity@ULH.nhs.uk. This includes sending copies of any e-mails you feel may be suspicious so action can be taken to block them if necessary.

